Market Analysis and Insights:
The market for Lawful Interception was estimated to be worth USD 3.81 billion in 2022, and from 2023 to 2031, it is anticipated to grow at a CAGR of 22.41%, with an expected value of USD 23.81 billion in 2031.
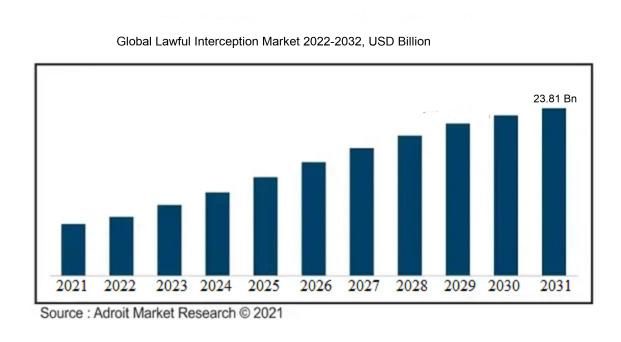
The Lawful Interception Market is influenced by three primary factors: government regulations and directives, escalating cyber security risks, and advancements in technology. Initially, government regulations and directives are pivotal in propelling the market forward by mandating telecommunication service providers to facilitate communication interception for legal reasons.
These regulations ensure that law enforcement agencies have access to essential information to prevent or investigate criminal activities. Secondly, the increase in global cyber threats has necessitated the adoption of more sophisticated surveillance capabilities, driving the demand for lawful interception solutions. Activities such as organized crime and terrorist operations conducted through digital communication channels call for advanced interception systems to detect and prevent such threats. Lastly, technological progress has a significant impact on the market, given the complexities of intercepting modern communication technologies such as mobile networks and internet-based platforms, making it challenging for law enforcement agencies. Therefore, continued innovation in interception solutions to adapt to evolving technological landscapes is crucial to meet the demand for effective lawful interception capabilities. In summary, these driving forces foster the expansion of the Lawful Interception Market as governments, organizations, and law enforcement bodies seek solutions to combat emerging security threats.
Lawful Interception Market Scope :
| Metrics | Details |
| Base Year | 2023 |
| Historic Data | 2018-2022 |
| Forecast Period | 2024-2031 |
| Study Period | 2018-2031 |
| Forecast Unit | Value (USD) |
| Revenue forecast in 2031 | USD 23.81 billion |
| Growth Rate | CAGR of 22.41% during 2023-2031 |
| Segment Covered | By Component ,By Network ,By Network Technology,By Communication Content ,By Mediation Device,By Type Of Interception,By End User, By Region . |
| Regions Covered | North America, Europe, Asia Pacific, South America, Middle East and Africa |
| Key Players Profiled | Cisco Systems Inc., Siemens AG, Verint Systems Inc., Utimaco GmbH, Aqsacom Inc., Ericsson AB, Netscout Systems Inc., SS8 Networks Inc., ZTE Corporation, and FireEye Inc. |
Market Definition
Legal interception pertains to the legitimate procedure of supervising and gathering communication information by duly authorized governmental entities in order to safeguard public welfare and thwart unlawful behaviors. It allows for the monitoring of various forms of communication such as phone conversations, electronic mails, and online activities, within specific legal guidelines.
Legal interception involves the authorized monitoring and interception of communications by law enforcement agencies to prevent and investigate crimes. It is a pivotal aspect of upholding national security and combating terrorism, cybercrime, drug trafficking, and other unlawful activities. Through legal interception, authorities can collect crucial evidence, identify suspects, and avert potential threats to public safety. By surveilling and intercepting specific communications, law enforcement agencies can acquire intelligence, predict criminal actions, and compile evidence for legal purposes. This process ensures a balance between the right to privacy and the necessity for public safety, enabling authorities to promptly and efficiently safeguard citizens and uphold law and order.
Key Market Segmentation:
Insights On Key Component
Solutions:
In the Global Lawful Interception market, the Solutions part is expected to dominate. This is primarily attributed to the increasing demand for advanced technological solutions that enable interception and monitoring of communication activities. Law enforcement agencies and government organizations are increasingly adopting lawful interception solutions to ensure public safety and combat criminal activities. These solutions offer capabilities such as data analysis, real-time monitoring, metadata extraction, and deep packet inspection, thereby providing efficient and effective interception capabilities to the authorities.
Services:
While Solutions take the lead, the Services part also plays a crucial role in the Global Lawful Interception market. These services encompass a range of offerings such as consulting, system integration, maintenance, and training. Lawful interception service providers offer expertise in implementing, managing, and maintaining the lawful interception infrastructure, ensuring smooth operations for governments and law enforcement agencies. These services help to augment the capabilities of the solutions deployed, ensuring optimal functioning and enhancing overall interception operations.
Insights On Key Network
Mobile Network
The dominating part among the By Network (Fixed Network, Mobile Network) in the Global Lawful Interception market is the Mobile Network. This trend can be attributed to the pervasive use of mobile devices and the growing adoption of mobile communication technologies worldwide. With the proliferation of smartphones and the growing demand for mobile internet services, law enforcement agencies are increasingly relying on the interception of mobile network communications to prevent and investigate crime. Consequently, the demand for lawful interception solutions for mobile networks is anticipated to experience substantial growth in the forthcoming years.
Fixed Network
The Fixed Network of the Lawful Interception market is another important part. Although it may not dominate the market, it still holds significance due to the continued usage of landline and wired communication systems in various regions and sectors. Organizations such as government agencies, emergency services, and critical infrastructure entities often rely on fixed network communication for their operations. Consequently, the need for lawful interception solutions in the fixed network remains relevant to ensure public safety and security.
Insights On Key Network Technology
Digital Subscriber Line:
The Digital Subscriber Line (DSL) segment is poised to lead the global lawful interception market. This is chiefly because DSL technology is extensively employed for internet connectivity, especially in residential and small business settings. Leveraging traditional copper telephone lines, DSL offers high-speed internet access, rendering it a favored choice among numerous consumers. As a result, the need for lawful interception capabilities in DSL networks is expected to drive the demand for related solutions and services.
Integrated Services for Digital Networks:
The Integrated Services for Digital Networks (ISDN) part is expected to have a significant presence in the Global Lawful Interception market. ISDN is a digital communication standard that allows the transmission of voice, video, and data over digital telephone lines or ordinary telephone copper wires. While the adoption of ISDN has declined in recent years, it is still widely used in certain regions for specific applications. As a result, lawful interception solutions catering to ISDN networks will continue to play a role in the market.
Long Term Evolution:
The Long Term Evolution (LTE) segment is anticipated to hold a significant portion of the Global Lawful Interception market. LTE stands as a wireless communication standard enabling high-speed data transmission across mobile networks. With the burgeoning usage of smartphones and mobile internet, LTE has emerged as the predominant technology in numerous countries. As a result, the need for lawful interception capabilities in LTE networks is expected to drive the demand for related solutions and services.
Public Switch Telephone Network:
The Public Switch Telephone Network (PSTN) part is predicted to maintain a significant presence in the Global Lawful Interception market. Despite the advancements in digital and mobile technologies, PSTN remains an essential part of the communication infrastructure, particularly for landline telephony services. Although the adoption of PSTN is gradually declining, the need for lawful interception in this network type continues to exist, contributing to the market demand for PSTN interception solutions.
Voice Over Internet Protocol:
The Voice over Internet Protocol (VoIP) segment is projected to secure a notable share in the Global Lawful Interception market. VoIP technology enables voice communication over the internet, offering cost-effective and flexible solutions for both personal and business use. As VoIP gains popularity as an alternative to traditional phone systems, the need for lawful interception capabilities in VoIP networks is likely to drive the demand for related solutions and services.
Wireless Local Area Network:
The Wireless Local Area Network (WLAN) part is projected to have a significant presence in the Global Lawful Interception market. WLAN refers to wireless networking technology commonly used for local area connectivity, such as in homes, offices, and public spaces. With the increasing adoption of wireless devices and the growing reliance on WLAN for internet access, the need for lawful interception capabilities in WLAN networks is expected to drive the demand for related solutions and services.
Worldwide Interoperability for Microwave Access:
The Worldwide Interoperability for Microwave Access (WiMAX) component is anticipated to sustain a substantial presence in the global lawful interception market. WiMAX serves as a wireless communication standard facilitating high-speed broadband access across extended distances. Though its adoption has been relatively limited compared to other technologies, WiMAX networks are still operational in certain regions, particularly for specific applications. This sustains the demand for lawful interception solutions catering to WiMAX networks.
Others:
The Others part within the Global Lawful Interception market comprises various network technologies beyond the mentioned options, such as satellite communication systems and emerging technologies. While the specific dominance of any particular part under this category cannot be determined without further analysis, it is crucial to monitor and address the lawful interception requirements of diverse network technologies. As technology advances and new network types are introduced, the need for lawful interception capabilities in these other networks is expected to drive the demand for related solutions and services.
Insights On Key Communication Content
Voice Communication is expected to dominate the Global Lawful Interception market. With the increasing use of voice communication in various applications such as telephone calls, voice-over IP (VoIP), and mobile communication, the demand for lawful interception of voice content is growing rapidly. Law enforcement agencies and governments require intercepting voice communication to prevent and detect criminal activities, ensuring public safety and national security. The ability to intercept voice communication provides valuable evidence in investigations. As a result, the voice communication part is projected to be the dominant part of the Global Lawful Interception market.
Video
The video part of the Global Lawful Interception market plays a significant role in monitoring and investigating criminal activities. Law enforcement agencies use video surveillance systems to capture and analyze video content for evidence collection. With the proliferation of video content in various sectors, including public spaces, transport systems, and commercial establishments, the demand for lawful interception of video has witnessed substantial growth. The video part is expected to contribute significantly to the Global Lawful Interception market, although it is not the dominating part.
Text Messaging
The text messaging part of the Global Lawful Interception market focuses on intercepting and monitoring text-based communication, including SMS and instant messaging applications. This part enables the lawful interception of text messages for investigative purposes, such as gathering evidence and detecting criminal activities. With the widespread usage of text messaging across personal and professional communication channels, the demand for intercepting text messages is considerable. While important, the text messaging part is not anticipated to be the dominating part of the Global Lawful Interception market.
Faxcimile
Although less prevalent than in previous years, fax communication remains a crucial means of transmitting documents securely. The faxcimile part of the Global Lawful Interception market caters to the interception of faxed content for investigative purposes. Law enforcement agencies and regulatory bodies may intercept faxes to gather evidence or monitor specific individuals or organizations. Despite its importance in specific contexts, the faxcimile part is not expected to dominate the Global Lawful Interception market.
Digital Pictures
The digital pictures part pertains to the interception of visual content in digital formats. It involves capturing and analyzing images and photographs for investigative purposes. Law enforcement agencies and intelligence organizations intercept digital pictures to identify suspects, gather evidence, and prevent criminal activities. Although valuable in certain cases, the digital pictures part is not projected to be the dominating part of the Global Lawful Interception market.
File Transfer
The file transfer part focuses on the interception of files exchanged between individuals or organizations. This includes intercepting data shared through email attachments, cloud storage services, and peer-to-peer file sharing platforms. Intercepting file transfers enables law enforcement agencies to uncover illicit activities and gather evidence for investigations. However, while integral to the Global Lawful Interception market, the file transfer part is not expected to be the dominating part.
Insights On Key Mediation Device
Intercept Access Point
The Intercept Access Point part is expected to dominate the global Lawful Interception market. The Intercept Access Point devices play a crucial role in intercepting and capturing communication data from network service providers. These devices facilitate the lawful interception of communication for authorized government agencies, assisting in criminal investigations and national security. Due to the escalating demand for surveillance and monitoring, the Intercept Access Point segment is forecasted to experience notable growth in the market.
Routers:
Routers are essential mediation devices in Lawful Interception, acting as the communication backbone between networks. They provide efficient data transmission and play a vital role in monitoring and intercepting communication. Although routers are an integral part of the Lawful Interception infrastructure, they are expected to have less dominance compared to the Intercept Access Point part.
Switches:
Switches are networking devices that connect multiple devices within a local area network (LAN). While they serve an essential function in network connectivity, their role in Lawful Interception is relatively limited compared to other mediation devices. Consequently, switches are not expected to dominate the global Lawful Interception market.
Gateway:
Gateways facilitate the interoperability of different communication protocols and networks, enabling smooth data exchange for Lawful Interception purposes. While gateways play an important role in connecting various systems within Lawful Interception infrastructure, they are not anticipated to be the dominating part.
Handover Interface:
Handover interfaces enable the seamless transfer of intercepted communication data between different service providers or networks. They allow uninterrupted monitoring and data collection, contributing to effective Lawful Interception processes. However, the Handover Interface part is not expected to dominate the global Lawful Interception market.
Management Server:
Management servers act as a central control hub for Lawful Interception systems, facilitating monitoring, data storage, and analysis. Although they are integral to the overall infrastructure, the Management Server part is not projected to be the dominating part within the global Lawful Interception market.
Insights On Key Type Of Interception
Passive Interception
Passive interception is expected to dominate the global lawful interception market. This type of interception involves monitoring communications without disturbing or intercepting the original data flow. It allows authorities to collect data and information from various communication networks, including voice, data, and internet traffic, without the knowledge of the targets. The increasing need for law enforcement agencies to combat criminal activities and terrorism is driving the demand for passive interception solutions. The ability of passive interception to monitor communications discreetly and efficiently is expected to contribute significantly to its dominance in the global market.
Active Interception
Active interception is another important part of the global lawful interception market. This type of interception involves intercepting and collecting data by actively accessing and disrupting the targeted communication networks. Active interception solutions allow authorities to intercept various communication modes, including voice calls, text messages, and internet traffic, by directing the data flow through a monitoring system. Although active interception offers extensive control and real-time access to intercepted data, its dominance in the market might be limited compared to passive interception. The potential legal and ethical concerns associated with active interception can restrict its growth and adoption.
Hybrid Interception
Hybrid interception, combining elements of both active and passive interception, is a part of the global lawful interception market. Hybrid interception solutions offer authorities the flexibility to choose between passive or active modes based on their requirements and objectives. They allow monitoring of communication networks while avoiding any disruption to the original data flow. Hybrid interception provides a compromise between the control offered by active interception and the discreet monitoring of passive interception. However, despite its advantages, hybrid interception is likely to have a smaller market share compared to passive interception due to the dominance of the latter in meeting the needs of law enforcement agencies.
Insights On Key End User
Lawful Enforcement Agencies
Lawful enforcement agencies are expected to dominate the global lawful interception market. This trend can be attributed to the growing adoption of interception solutions by law enforcement agencies worldwide to combat criminal activities and uphold public safety. The rising incidence of cybercrimes, terrorism, and illegal activities has led to a growing need for advanced interception technologies and solutions. Lawful enforcement agencies, including police departments, intelligence agencies, and regulatory bodies, are actively investing in and implementing these solutions to monitor and intercept communications for investigation and evidence collection purposes. As a result, the lawful enforcement agencies is likely to be the dominant part within the global lawful interception market.
Government
While lawful enforcement agencies are projected to be the dominant part, the government sector also plays a significant role in the global lawful interception market. Governments across the world are actively involved in implementing interception solutions to maintain national security, protect critical infrastructure, and prevent unauthorized access to sensitive information. The government part includes government departments, defense organizations, and intelligence agencies that utilize lawful interception solutions to gather intelligence, counter espionage, and protect national interests. Though not as dominant as the lawful enforcement agencies part, the government sector remains a substantial player in driving the demand for lawful interception technologies.
Insights on Regional Analysis:
North America
North America is expected to dominate the global lawful interception market. This can be attributed to the high adoption rate of advanced technologies, such as cloud computing and IoT, in this region. Furthermore, the presence of major players in the market and stringent regulations pertaining to lawful interception in countries like the United States and Canada are contributing to the dominance of North America in the global market.
Latin America
Latin America is witnessing significant growth in the lawful interception market. The increasing usage of smartphones and internet services, along with the rising concern for national security, is driving the demand for lawful interception solutions in countries like Brazil and Mexico. Furthermore, government initiatives aimed at enhancing cybersecurity measures are anticipated to further bolster market growth in this region.
Asia Pacific
The Asia Pacific market for lawful interception is experiencing rapid expansion as digital technologies gain broader adoption across various industries. Countries such as China and India play a significant role in driving market growth in this region. The proliferation of telecom networks, coupled with the rising incidence of cybercrime, is spurring the demand for lawful interception solutions. Moreover, escalating investments in advanced telecommunications infrastructure and the enforcement of stringent lawful interception regulations by governments are poised to further propel market growth in Asia Pacific.
Europe
Europe is witnessing substantial growth in the lawful interception market, driven by a ened emphasis on cybersecurity and the presence of stringent regulations governing lawful interception. Countries such as Germany, France, and the UK are leading in terms of adopting advanced surveillance technologies. The escalating instances of cyber threats and the imperative for robust monitoring and surveillance solutions are fueling the demand for lawful interception in this region.
Middle East & Africa
The Middle East & Africa region is witnessing steady growth in the lawful interception market. The increasing usage of communication devices and the rising instances of security breaches are driving the demand for lawful interception solutions in this region. Governments in countries like the UAE, Saudi Arabia, and South Africa are implementing strict regulations regarding lawful interception to ensure national security. Additionally, the Middle East and Africa region are poised for market growth due to increasing investments in advanced communication infrastructure and a growing awareness of the importance of surveillance.
Company Profiles:
Major stakeholders in the global lawful interception industry have a significant impact by offering state-of-the-art surveillance solutions and technologies to various law enforcement agencies and intelligence entities globally. Their focus is on pioneering the development of sophisticated interception systems, lawful interception gateways, and analytical instruments to aid in the lawful monitoring and access of communication data.
Prominent figures within the Lawful Interception Market comprise Cisco Systems Inc., Siemens AG, Verint Systems Inc., Utimaco GmbH, Aqsacom Inc., Ericsson AB, Netscout Systems Inc., SS8 Networks Inc., ZTE Corporation, and FireEye Inc.
COVID-19 Impact and Market Status:
The lawful interception market on a global scale has experienced effects from the Covid-19 pandemic, causing disturbances in supply chains and a decrease in the need for surveillance technologies.
The global impact of the COVID-19 pandemic has infiltrated various sectors, notably the lawful interception industry. This industry entails the authorized tracking and surveillance of telecommunications for the purposes of law enforcement and national security. The pandemic has presented novel hurdles for governments and law enforcement bodies in effectively monitoring and intercepting telecommunications activities due to the surge in remote work and data communication. While the demand for lawful interception solutions may have escalated to monitor potential threats, the market may also have faced setbacks from the economic downturn triggered by the pandemic. This could have led governments and organizations to reallocate resources to address more pressing concerns. In light of the uncertain duration and aftermath of the pandemic, stakeholders in the lawful interception sector must be proactive in adapting to the changing landscape and addressing the evolving needs and challenges posed by law enforcement agencies and national security entities.
Latest Trends and Innovation:
- In August 2021, SS8 Networks announced the acquisition of McArthurGlen designer outlets' telecommunications infrastructure to enhance its Lawful Interception (LI) solutions.
- In June 2021, Verint Systems collaborated with Atos to integrate their lawful interception and compliance management capabilities to deliver comprehensive LI solutions for service providers.
- In April 2021, Verint Systems partnered with Aqsacom to enhance their LI offerings by integrating Verint's network recording and Aqsacom's lawful interception capabilities.
- In February 2021, Utimaco, a global provider of professional cybersecurity solutions, acquired Realsec, a Spanish IT security company, to expand its LI portfolio.
- In November 2020, Verint Systems acquired Cognyte Software to further bolster its LI and intelligence solutions.
- In September 2020, SS8 Networks launched a new version of its Xcipio mediation platform to provide advanced LI capabilities for a wide range of networks.
- In August 2020, Utimaco partnered with Rohde & Schwarz Cybersecurity to offer comprehensive end-to-end LI solutions for telecommunication companies.
- In July 2020, SS8 Networks introduced its advanced Intellego XT solution for 5G lawful intelligence and interception.
- In May 2020, Utimaco partnered with VAD Technologies to expand its presence in the Middle East's LI market and provide robust LI solutions to regional customers.
- In February 2020, Verint Systems introduced its AI-powered Intelligent Virtual Assistant (IVA) solution, which includes built-in LI capabilities.
Significant Growth Factors:
Factors fueling the expansion of the lawful interception sector comprise the growing occurrence of cybercrimes, escalating anxieties regarding national security, and the enforcement of strict governmental policies.
The market for Lawful Interception (LI) is poised for substantial growth in the foreseeable future, propelled by various key drivers. Primary among these is the ened concern surrounding national security and the imperative to counter threats posed by terrorism, criminal activities, and cyber risks. Law enforcement and intelligence agencies globally are increasingly turning to LI technology to monitor and intercept communication data in support of investigative operations. Another significant factor fueling this growth is the widespread usage of internet services and the rapid adoption of digital devices like smartphones, leading to a substantial increase in data traffic volume. This surge in communication data underscores the need for advanced LI solutions capable of efficiently intercepting and analyzing large data volumes in real-time. Moreover, government efforts to enhance regulatory frameworks and compliance standards for telecom operators and internet service providers are expected to further drive the expansion of the LI market. The escalating demand for cloud-based services and the shift towards IP-based networks are also contributing to the need for sophisticated LI solutions that can effectively intercept and monitor communication data within these environments.
Moreover, technological advancements, especially in domains like deep packet inspection, data analytics, and machine learning, are augmenting the capabilities of LI solutions, facilitating more precise and efficient interception functionalities. Collectively, these growth catalysts present a favorable growth trajectory for the Lawful Interception market, offering substantial opportunities for stakeholders within the industry.
Restraining Factors:
Constraints in legal regulations and considerations regarding personal privacy serve as impediments for the Lawful Interception Market.
The market for Lawful Interception, which pertains to monitoring and intercepting communication for legal and security purposes, has experienced notable growth in recent times. Nonetheless, there are several challenges that may influence its future expansion. A key obstacle is the rising adoption of encryption technologies by individuals and organizations, rendering it challenging for law enforcement agencies to intercept and access communication data. Furthermore, there are apprehensions regarding privacy and civil liberties, with concerns that extensive communication monitoring could encroach upon individual rights. The shifting regulatory environment, characterized by more stringent data protection laws and privacy regulations, also presents hurdles for providers of lawful interception solutions. Additionally, the proliferation of over-the-top (OTT) communication services and cloud-based platforms further complicates the interception process. These factors, along with the high implementation costs of lawful interception systems and the necessity for continual upgrades to stay abreast of technological advancements, pose obstacles to market expansion.
Nevertheless, despite these obstacles, there are encouraging developments on the horizon for the Lawful Interception Market. The escalation in cybercrime, terrorism, and other illicit activities has fueled a ened demand for advanced lawful interception solutions capable of effectively combating these threats. The increasing deployment of surveillance technologies by governments worldwide to uphold national security and public safety is anticipated to propel market growth in the years ahead. Furthermore, progress in technologies like artificial intelligence, machine learning, and big data analytics are enabling more efficient interception and analysis of communication data. These technological strides, in conjunction with ongoing research and development endeavors in the domain, offer promise for the future of the Lawful Interception Market, notwithstanding the prevailing restraining factors.
Key Segments of the Lawful Interception Market
By Component
- Solutions
- Services
- By Network
- Fixed Network
- Mobile Network
By Network Technology
- Digital Subscriber Line
- Integrated Services for Digital Networks
- Long Term Evolution
- Public Switch Telephone Network
- Voice Over Internet Protocol
- Wireless Local Area Network
- Worldwide Interoperability for Microwave Access
- Others
By Communication Content
- Voice Communication
- Video
- Text Messaging
- Faxcimile
- Digital Pictures
- File Transfer
By Mediation Device
- Routers
- Switches
- Gateway
- Handover Interface
- Intercept Access Point
- Management Server
By Type Of Interception
- Active Interception
- Passive Interception
- Hybrid Interception
By End User
- Lawful Enforcement Agencies
- Government
Regional Overview
North America
- US
- Canada
- Mexico
Europe
- Germany
- France
- U.K
- Rest of Europe
Asia Pacific
- China
- Japan
- India
- Rest of Asia Pacific
Middle East and Africa
- Saudi Arabia
- UAE
- Rest of Middle East and Africa
Latin America
- Brazil
- Argentina
- Rest of Latin America
Frequently Asked Questions (FAQ) :

